The Security Measure iPhone Owners Need To Take
Early Tuesday, a number of Australian iPhone and iPad owners awoke to find their devices locked, with an alert asking for $50 to $100 to give access back. The lesson: It’s easier than you think for someone to get into your Apple products — even if a thief doesn’t have the actual iPhone in his or her hands.
One way to make yourself that much safer? Start using two-step verification for your Apple ID.
When you enable two-step verification, Apple will make you prove you’re actually you whenever you buy anything on iTunes, the App Store or the iBooks Store. It works like this: Apple will text you a code anytime you try to sign into your Apple account to make a purchase. You will then have to input that number to verify your identity. That way, nobody else can access your account unless they have both your password and your device, making it far more difficult to steal your identity and credit card information.
Here’s how you do it:
First, go to the Apple ID site, click “Manage your Apple ID” and sign in. From there, click “Password and Security.”
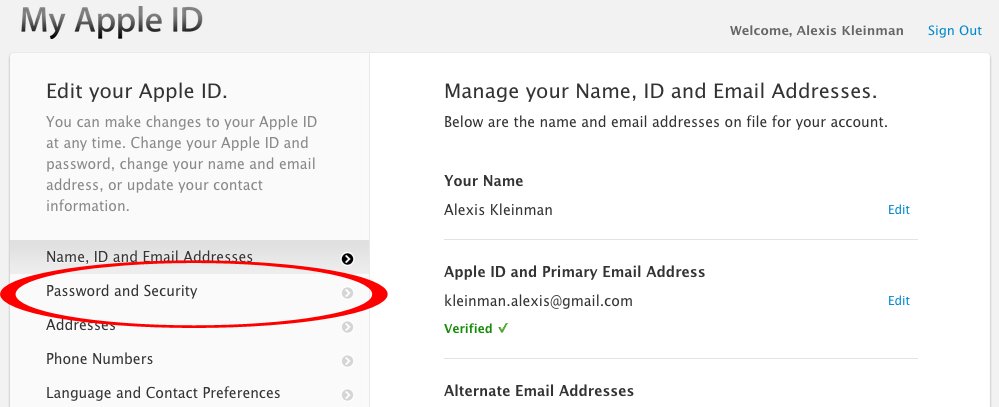
From there, you’ll see “Two-Step Verification.” Under that you should click “Get started…”
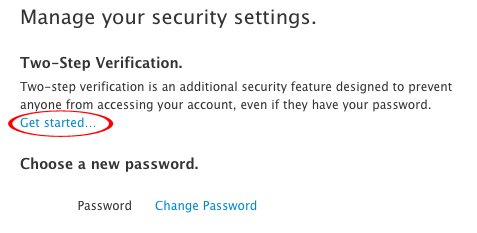
There you’ll be able to sign up for two-step verification. For security reasons, Apple makes you wait three days after setting up two-step verification for it to take effect. Once you sign up, you’ll get an email telling you exactly when you’ll be able to use it.
Once you have two-step verification, this is how it works when you sign into Apple to make a purchase:
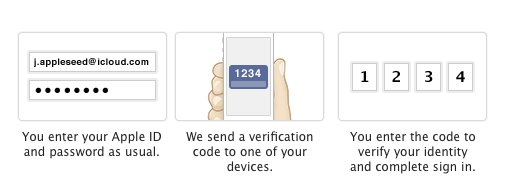
You’ll also get a Recovery Key, which is a 14-digit series of numbers and letters that you can use to access your account if you ever lose access to your iPhone and are unable to receive text messages. Apple recommends you print our your Recovery Key and keep it in a safe place.
Many people don’t think about Apple security — even though the devices and accounts can contain a ton of personal information. Half of iPhone users don’t even use their phone’s regular passcode, and some people probably still haven’t updated their iPhones after a major security flaw was discovered in February. Two-step verification is just one extra way you can protect yourself.



